14.67 Trillion Centuries To Hack Our Passwords: The Surprisingly Simple And Secure Paessler Password Policy
 Originally published on May 26, 2017 by Greg Campion
Originally published on May 26, 2017 by Greg Campion
Last updated on March 03, 2022
•
10 minute read
I had been working at Paessler for about a year as a systems administrator when we decided to do a security audit. This consisted of many interviews with us systems administrators, and right at the beginning one of the first questions the auditor asked was, "So what is your password policy?" All three of us chuckled a bit and said flatly, "We don't have one."
There were only around 60 employees at that point, so we had thought we could simply trust everyone to change their passwords every now and again. Once we reviewed the age of our users' passwords, we found out that many of our employees hadn't changed their password since the company was founded!
Every systems administrator who has had to implement a password policy knows how annoying it can be when users who are not technical complain that "There's no way I can remember this password, then create a new one in 6 months and then remember that!" and technical users say, "You know that forcing users to change passwords every six months doesn't accomplish anything, I'll send you 10 articles that prove it."
When they say this though, all you can do is shake your head because the fact of the matter is, changing your password may not be "necessary" and depending on how you implement it, a password policy may in fact be less secure, but it usually isn't your choice, it's a requirement of different standards or processes.
The point of this post is not to debate whether a password policy makes sense or not, since we system administrators often don't have a choice, we only have the task of implementing it and bringing down the wrath of techie and non-techie alike. With that said, here are the reasons and the logic behind the password policy we implemented at Paessler.
Our password policy is simply that your password must be over a certain amount of characters. That's it. Really. This may sound to some illogical or far too simple, but it's actually mathematically and sociologically proven that longer passwords are the most effective passwords.
This is for 2 main reasons:
1. If you enforce password rules like a special character requirement, a capital letter requirement, or that users cannot use repeating characters, the only thing that you have accomplished is that some of your users (you know which ones) will write it on a Post-it note and leave it out in the open, which means that anyone capable of reading can access your network.
2. Most password hacking tools are brute force attacks. This means that they try the most common passwords first and then will start guessing random words with special characters, capital letters and non-repeating characters with the most common special characters, like an exclamation point at the end. Since that's the case, the thing that matters most about a password policy is that it forces users to use longer passwords.
One of the biggest issues with a corporate network that is using Active Directory is that the password policy is standardized and is an all or nothing policy.
iActive Directory (AD) is a directory service created by Microsoft for use in a Windows Server environment. It provides authentication and authorization functions, as well as providing a framework for other such services. The directory itself is an LDAP database that contains networked objects. Active Directory uses the Windows Server operating system. Read more ...
When setting that group policy, you can either enable password rules with complexity or not. When enabled these are the requirements according to Microsoft's TechNet:
The password contains characters from three of the following categories:
- Uppercase letters of European languages (A through Z, with diacritic marks, Greek and Cyrillic characters)
- Lowercase letters of European languages (a through z, sharp-s, with diacritic marks, Greek and Cyrillic characters)
- Base 10 digits (0 through 9)
- Non-alphanumeric characters (special characters) (for example, !, $, #, %)
- Any Unicode character that is categorized as an alphabetic character but is not uppercase or lowercase. This includes Unicode characters from Asian languages."
It does allow for Unicode, which is good since that allows for people who speak languages other than English to use a password that makes sense to them, but otherwise makes passwords utterly unremarkable.
That's why when we made the password policy here at Paessler, we decided that the length of people's password was more important and decided to trust our users to not use passwords that can be guessed easily. We also educated all of our current users about passwords and each time someone starts with us, we mention this as we are setting up their workstations. When you explain to a user that using a few words with spaces will make their passwords more secure, memorable, and the company less hackable, they are usually a lot more open to new password policies.
The reason why password length matters is because of something called information entropy. You can think of information entropy as a measurement of how unpredictable a password is, and thus measures how long it would take a computer to guess it through brute force attacks. The longer the password is, the more "bits"of information entropy it has, and the longer it will take to guess, provided it's not something inane like "aaaaaaaaaaaaaaa" since those kinds of passwords will be guessed first in a brute force attempt.
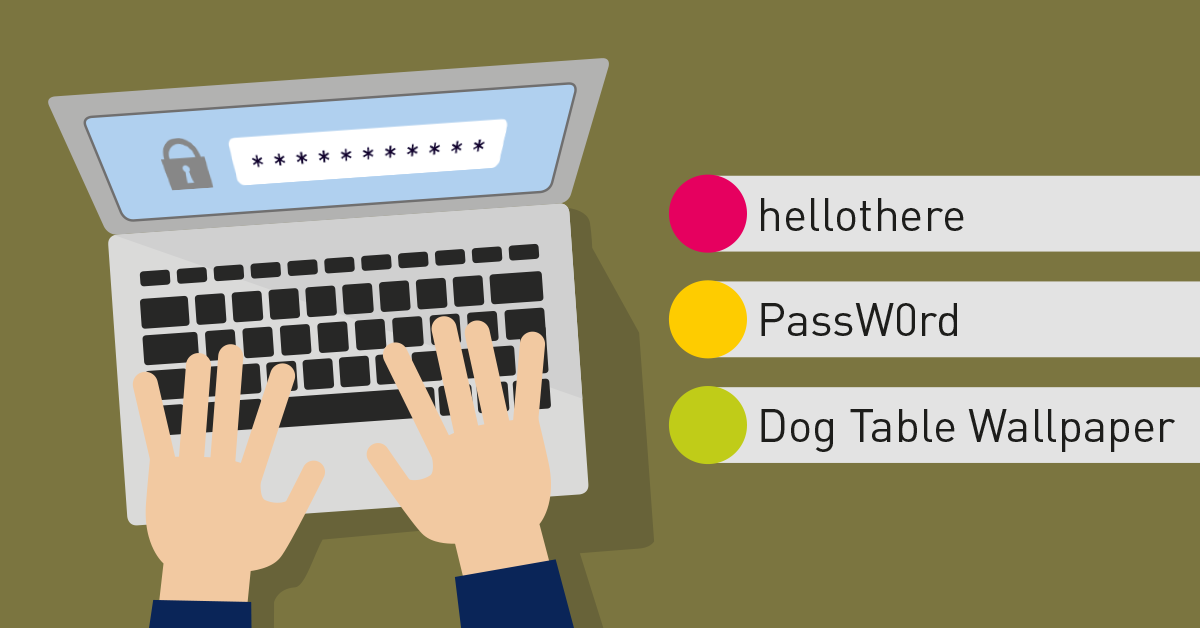
For example, if you have a password that is 8 characters long and has two normal words in it like "hellothere", a modern password cracker will take around 1.5 seconds to crack it. A password of 'password' just over .02 seconds. A fancier one like "Passw0rd!" will take around 1.7 hours and although it meets the complexity requirements of Active Directory, it is still incredibly easy to crack. A password of "Dog Table Wallpaper", however, would take roughly 14.67 trillion centuries.
These numbers are based on the calculator here.
As you can see, if you set your Active Directory password policy to require more than 10 characters, your users should be able to remember their passwords more easily, since humans weren't made to remember passwords like "VZ4h#253QqI&mb1iyD6#", and they become vastly more complicated to crack with a brute force attack. Until AD can support better password policies natively, like checking for easy-to-guess passwords and simplified rules, setting a minimum password length and educating your users is really the way to go.
If you want to read more about the topic, here are some other great links:
http://www.thebitmill.com/articles/password_length.html
http://resources.infosecinstitute.com/password-security-complexity-vs-length/#gref